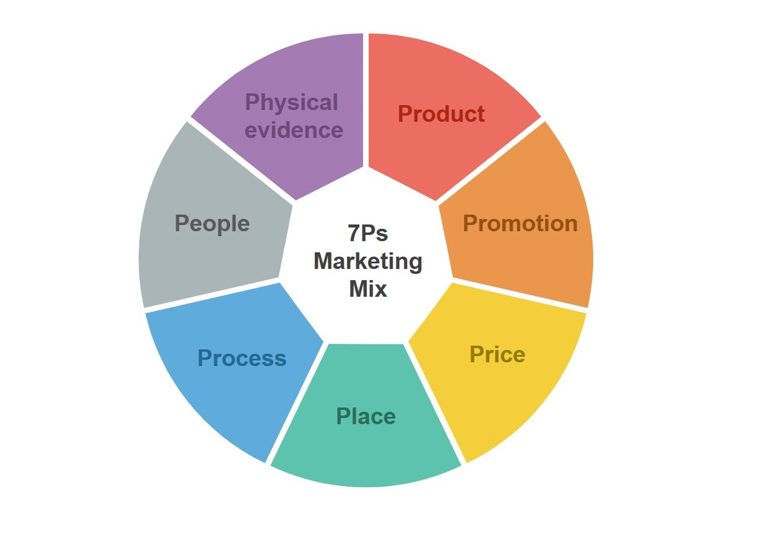
The RMIT experts proposed implementing the seven “Ps” as follows:
1. Product
The product marketed by the strategy is the employees’ participation in creating a safe and secure cyber environment. The employees are expected to clearly understand their responsibility and be able to consistently perform cyber security measures, while minimising any waste of effort or time.
2. Promotion
In order to encourage employee engagement, the content should be tailored to each department and relate to their immediate interests. Also, policies should be unambiguous, and guidelines simple and easy to follow. The content should be designed in a way that is intuitive and interactive, and social media can be a useful channel to amplify the messages.
“Organisations should let users practice security requirements in realistic situations that reflect the nature of their department’s work, since most employees only implement security measures that directly affect their work," Dr Hiep noted.
3. Price
According to the RMIT experts, most employees understand costs as the time and effort they spend on implementing cybersecurity, as well as the loss of productivity. However, the financial costs (for example, to contain a data breach or pay legal fees) and reputational damage caused by cyber attacks to the organisation are not as clearly understood, and thus must be made known to the users too.
4. Place
Cyber security compliance (or non-compliance) behaviours mainly take place on digital channels. It is critical to identify and manage these locations so that the organisation can build necessary measures and train their employees' awareness, as well as ensure that support is available for any situation.
5. Process
Processes can be both a facilitator and a barrier to cyber security. If processes are too complicated, the users might lose motivation or face difficulties in complying. Yet, too simple processes might not be able to withstand attacks from outside.
“The employees and management can co-create the processes. Integrated procedures should be built, personal interactions should be increased, and users should get help navigating cyber security processes by themselves through online training, handbooks, virtual helpdesks, and the like,” Dr Hiep proposed.
6. People
People are the ones who can “make or break” the cyber security system. To raise employee participation, Dr Hiep and his colleagues think that organisations need to provide effective IT support. Thus, they can reduce work disruptions and increase employee satisfaction.
7. Physical evidence
The final key element is the evidence to help remind users of the risks and consequences from a lack of information security. Specific evidence should be placed around the employees’ work area and serve as a reminder of the risks and consequences of security non-compliance, as well as the responsibility of each employee.
“Ensuring compliance with cyber security policies requires a lot of engagement with employees. Internal social marketing using the 7P marketing mix offers a simple way to do this,” Dr Hiep concluded.
Story: Ngoc Hoang